Blockchain Basics
Blockchain is a time-stamped series of immutable records of data that is managed by a cluster of computers not owned by a single entity. Transactione is the basic element of the bitcoin blockchain. Many transactions form a block. Transactions are validated & broadcast. Blocks go through a consensus process, to select the next block that will be added to the chain. Chosen block is verified & added to the current chain. Validation & consensus process are caried out by special peer nodes called miners. These powerful computers executing software is defined the blockchain protocol.
Types of blockchains :
- Only cryptocurrency –> ex : Bitcoin
- currency + Business logic –> ex : Etherium
- Only Business logic –> ex : Linux foundation’s Hyperledger
Bitcoin
Unspent Transaction Output (UTXO) are referenced as inputs in a transaction and are also output generated by a transacton. UTXOs in a bitcoin network is collectively defined by the state of Bitcoin Blockchain. All the UTXOs are stored the participant nodes in a database. A transaction generates new UTXOs for transfersing the amount specified in the input UTXOs.
Bitcoin store data about transactions & user balances in the form of UTXO, which are a list of unspent Bitcoin amounts that a user have sent, bat have not yet been sent from him/her. The sum of these outputs is the user’s total balance.
Basic operation in a blockchain creation
- Validation of transactions
- Gathering transactions for a block
- Broadcasting valid transactions & blocks
- Consensus of next block creation
- Chaining blocks
Roles of miners
- Verify transactions (Tx)
- Broadcast transactions
- Compete to create a block
- Reach consensus by validating block
- Broadcast new block
- Confirm transactions
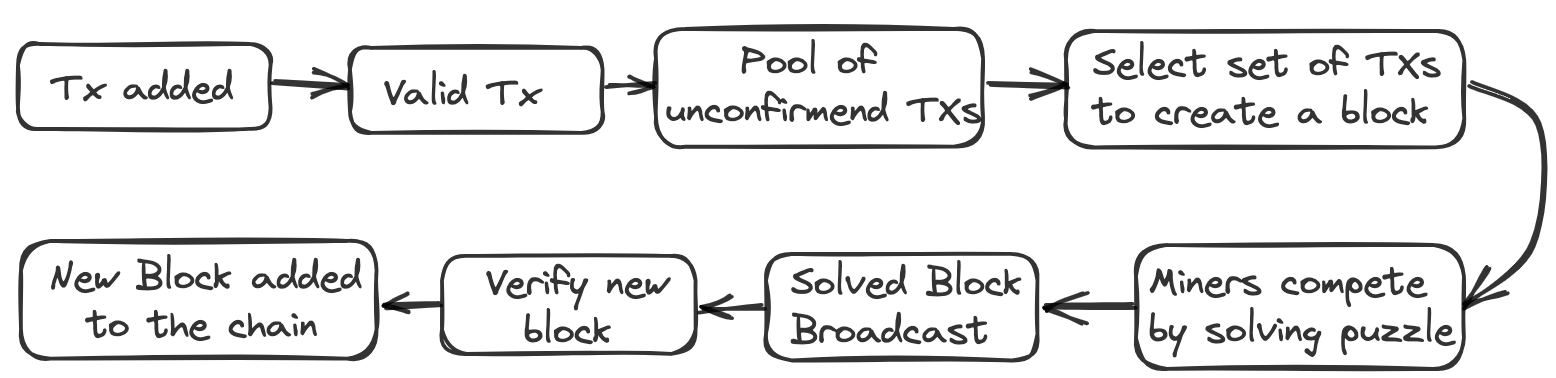
Blockchain creation operations
Coinbase Transaction : 0th transaction in every block in the bitcoin blockchain is for paying the miner fees and it doesn’t have any input UTXO.
Etherium
Smart Contracts are basic units of etherium protocol. A transaction in etherium includes :
- Recipient
- Signature of sender authorizing transfer
- Amount of wei
- Message to a contract
- Start gas (max no of steps)
- Gas price ( fee for computatian)
Gas spent : Actual amount-spent at the creation of block creation.
Gas limit : The amount of gas points available.
No. of transactions in a block = (Gas limit)/(Transaction Fee)
$$ 1 ether = 10^{18} Wei $$
Cryptography
Two techniques are predomimently used for securing the chain & for efficient validation & verification that is hashing & asymmetric Key eneryption.
Symmetric key encryption
In this case same key is used for encryption & decryption.
Ex. Caeser encryption :- Aphabets of a message fixed by a fixed number. And fixed no is the key.
Asymmetric key encryption
Examples for this includes : Rivest Shamir Adelman (RSA) Algorithm , Elliptic Curve Cryptography (ECC). ECC is used in Bitcoin and Etherium for generating key pair. ECC is a stronger encryption than RSA.
For a given number of bits :
256 bits of ECC key pair ≈ 3072 bits of RSA key pair
Hashing
A hash function(one way function) or hashing transforms and maps an arbitary lenght of input dala value to a unique fixed length value.
Ex. SHA-256, SHA-3, keccak-256, etc
- Keccak 256 is commonly used algorithm for hash generation in etherium block chain.
- Simple hash is used when there is fixed number of items to hashed such as items in a block header and we ase verifying the composite block integrity.
- Tree-structed hash function is used when there is a variable number of items to be hashed such as state changes in a block.
In etherium hashing is used to generate :
- Account address
- Digital Signature
- Transaction Hash
- State Hash
- Reciept Hash
- Block Header Hash
Transaction Integrity
Combination of public-key cryptography & hashing is used. Address of an account is generated with following steps-
- 256-bit random number = private key
- ECC algorithm applied to private key to generate public key
- Hashing applied to public key –> we get account address (20 bytes)
Integrity of a Block
- Block header content not tampered with.
- Transactions not tampered with.
- State transitions are computed, hashed and verified.
In etherium, the block hash is the hash of all the elements in the block header. Block hash allows for the formation of chain link by embedding previous block hash in the current block header. If a participant node tempers with a block, it results in mismatch of hash values and local chain of node rendered in an invalid state.
Digital signing of a transaction/document involves, hashing the content of document & then encrypting it with private key. Digital Signature supposts both user authentication & integrety of messages. A valid digital signature give a recipient reason to believe that message was created by a known sender (authentication), that the sender can not deny having sent the message, and that the message was not altered in transit (integrety).
Consensus Protocol
A consensus mechanism is a way for computers in a decentralized network to agree and trust each other. It helps them reach an understanding about the network’s state and transactions, ensuring security and preventing fraud.
Proof of Work (PoW) is the consensus protocol used by bitcoin and etherium blockchain.

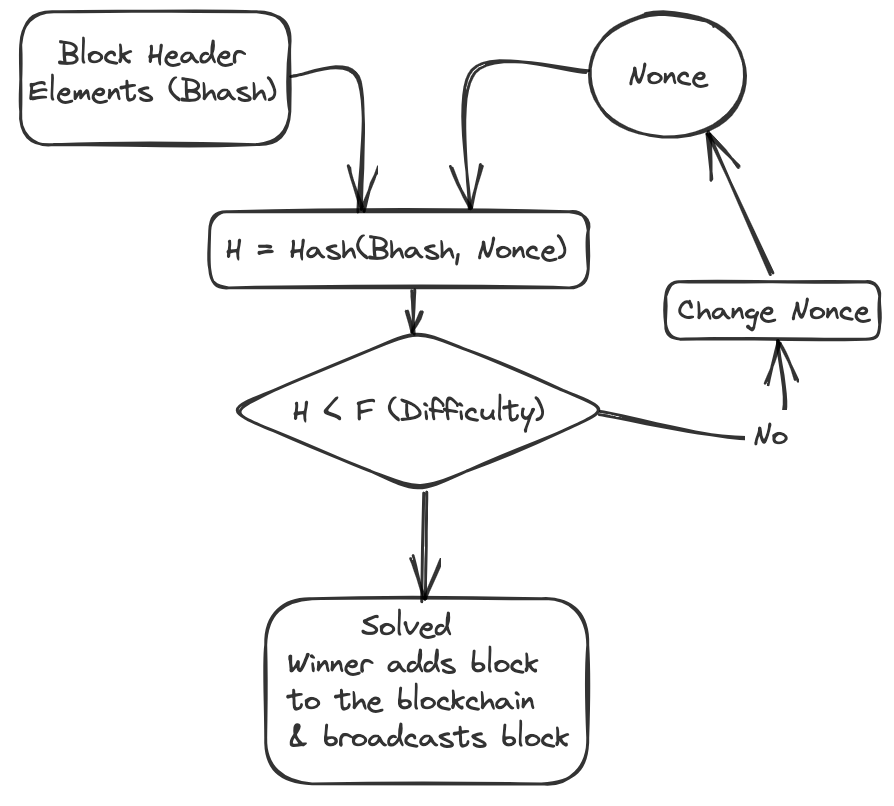
Concensus Protocol
Double Spending
When more than 1 transaction references as input to the same digital asset.
How to tackle double spending problem ?
- In bitcoin : It allows the 1st transaction that references the digital asset and reject rest of the transactions.
- In etherium : A combination of account number and a global nonce is used to address the double spending issue. Time spend on the nonce should be unique and prevent any double use of digital asset.
What happens when two miners have solved the consensus puzzle very close to each other?
- In Bitcoin : In that case, bitcoin protocol allows this chain to split or two chains for the next cycle. One led by each of the competing blocks. The probability that the next block will happen at the same time in both these chains is extremely low. So, the winner of next cycle or block creation consolidate one of the chains and that chain becomes the accepted chain. Now this chain is the longest and valid chain.
- In Etherium : Etherium handles more than one person by allowing omar or runner-up blocks and allocating a small incentive for these runner-up blocks.